Robots have gained a lot of importance and relevance in society with the implementation of Artificial Intelligence. Robots are increasingly performing security framework. Robot Security is being underestimated. Robot security framework is a methodology to perform systematic security assessments in robots. With the help of the proposed framework in this article, a user can propose, adapt and develop specific terminologies and provide guidelines to enable a security assessment with four main layers called Physical, Network, Firmware and Application layers.
Robot Security Framework:-
Robots are going mainstream, it is included in every stream starting from assistance to entertainment. Robotics is the next technological revolution. Robot security framework is an emerging challenge that needs to be addressed immediately. In this article, we will be proposing a robot security framework with four layers that are relevant to robotic systems.
The schematic framework representation is mentioned below:
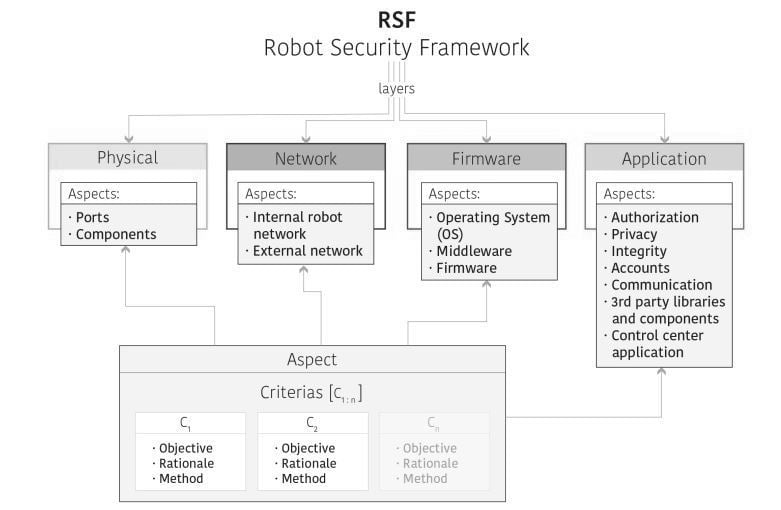
The proposed Robot security framework includes following layers:
1. Physical
2. Network
3. Firmware
4. Application
Physical Layer:
The physical layer identifies the ports and components aspects which can be analysed with specific criteria. In this layer, robot components can potentially lead to exposure of internal communication ports. Internal communication ports are not protected in this layer. This layer may serve as an entry point and allows attackers in physical proximity.
The security features of ports in physical layer is decided with factors with Objective, Rationale and Method.
Analysing the security features of external and internal communication ports is described below:
Objective:
The main objective is to verify if attackers or hackers can sniff or modify the critical data during communication with station or by connecting to the ports.
Rationale:
Unprotected external and internal communication ports can create scenario for intruders to perform variety of attacks by serving as an entry point.
Method:
1. Try to connect the identified communication ports
2. Determine whether the authentication is required.
3. Verify whether the message to be communicated is encrypted.
4. Try communicating through these ports to check if the robot’s state is affected.
Now its turn for analysing the security features defined in components in physical layer is described below:
Objective:
The main objective of this section is to analyse the internal hardware is accessible from outside.
Rationale:
To get the directly accessible components which can be physically damaged, stolen or tampered causing robot to misbehave. The best example for analysing the components is removal of critical sensors for the behaviour of robot.
Method:
1. Inspection of robots and verify for accessible components.
2. Open all the doors which do not include any protection and look for accessible components inside.
For the physical layer, it is important to note that all cables should remain inside robot. Some components should be kept outside body frame. It is always important to verify the logs of the robot and look for tampering actions.
Network Layer:
The network layer includes the internal and external factors which can be analysed with the corresponding criteria.
Objective:
To determine and access the network accessibility and the corresponding protection mechanisms.
Rationale:
Internal networks in the robot frameworks should be password protected with proper authentication check. External frameworks which communicate with Robot framework should include encryption procedure.
Method:
1. To validate the authentication mechanisms and verification with no known vulnerabilities.
2. Internal networks should be password protected with no usage of common passwords.
3. Verification of robot logs should be maintained with successful and unsuccessful attempts.
Firmware Layer:
This layer is designed to work on security features of operating system. It verifies the aspects of operating system updates.
Objective:
The main objective of this firmware layer is to verify that the used operating system(OS) is supported by the manufacturer and there are no system updates in near future.
Rationale:
Operating system includes a lot of security vulnerabilities.
Method:
1. Verify if the operating system is maintained and can respond to the security patches.
2. Verify if the security updates are of latest versions and are applied.
3. Verify if the update mechanism is present and enabled.
4. Verify if the updates undergo the authentication process and transferred as and when needed.
Application Layer:
The application layer of this framework includes authorization, privacy, integrity and communication between parties.
Objective:
The objective of this layer is to verify that resources are accessible to authorized users and services.
Rationale:
Provide access to the restricted functions by anonymous users or users with lower access rights or credentials.
Method:
1. Access with the authorized credentials and attempt to perform different records and maintain the track of requests being made.
2. Verify log out and log in activities to maintain the session activities. To send the requests as an unauthenticated user to check if the requests are handled properly.
3. Verify log out and log in activities of a user with lower access rights. Verify the process is successful.
Conclusion:
In this article we focussed on Robot Security Framework (RSF) which is used as a standard methodology that enables holistic evaluation of robot security. With the help of four layers which is involved in the proposal we can address robot security systematics. It finds a solution for major concerns such as robot privacy, integrity and security features. A deep understanding of the layers involved in the framework will play a crucial role to provide an integrated assessment for robotics.



