Introduction to cyber crime
Many organizations don’t even care about pros and cons of dealing with cybercrimes, some of them are product based companies while others are solution providers (specially dealing with web based and desktop based application). The situation becomes critical when often many organizations deal with disadvantages like data theft and hacking of systems (except ethical hackers). Many organizations are now a days moving towards analyzing data vulnerabilities and they are conducting regular data auditing, including managing a record of regular audits. They are implementing various tools, techniques and team of highly experienced professional in order to keep their data secure. Some organizations are also involved in personally identifiable information (PII) that has a very high and secure level of dominated protection organized by data privacy laws. Cybercrimes also include internal and external threats. That has to be managed using high amounts of data audits and firewalls or other protection based software.
Big data analysis cyber crime
There are some instances where big data analytics is pretty much helpful in identifying various cybercrimes including internal threats and external attacks. Modern malware attacks (attacks that are based on entering a system and slowly stealing critical information). An example would be of supply chain security big data analytics helps in identification of suppliers by scanning various data roots such as personal contacts, service level agreements (SLA), vendor management systems (for exploring various unstructured data sources), log reports, and big data analysis is highly suitable for analyzing and scanning network thus has a high chance of increasing the data theft identification factor. While considering internal threats, big data is highly useful and helpful in identifying the pattern of work and behavioral as well as sentimental analysis of the staff members of an organization.
How big data is helpful in fighting cyber crime
There are many instances where big data is helpful in fighting cyber-attacks and infringement of cyber laws; with the help of unstructured and complex data analytics we can easily identify flaws and errors in order to improve the efficiency and capability of one organization.
- Banking profile frauds detection: Profiling detection of intruders succeeded because many of the intruders (insider’s threat) never took off leave for more than few days, this means that now a fraud could not be concealed in an individual absence.
- Proliferation of mobile devices: Many of the remote and handheld devices are accessed in public as well as in most of the organization. Big data analysis could help in identifying staff by accessing their network traffic and time duration that a particular employee or a person is using, this helps in identifying the performance of an employee in an organization.
Techniques used for cybercrime detection
The prime focus in this technique is to detect the data that contains malicious contents (that can harm the servers or local workstations). These malicious viruses always attempt to compromise the security of machines.
Possibilities of a cyber-attack through emails
- Malware and phishing attacks like poisoned attachments (custom PDF exploits).
- Linking the outbound of a website (links going out of a website) to malwares and malicious data
- Installation of Trojans using remote access and fake software installations
- Fake domains like PayPal.com (Using I and not L)
- Hosted malicious software for cyber-attack in order to increase a chance of a user accessing a server and getting harmed.
- Spear Phishing: This term is used to attack a specific group or community.
Possible solutions for restricting cyber attacks
Some of the key tools include Q Radar security platforms that provide a comprehensive platform and integrated approach for combining real time correlation for continuous invigilation and customized analytics (writing our own customized Hadoop jobs for variety of analysis). The conjunction of these technologies can help in detecting advance persistence threats and internal risks and threats as well. It has widened the scope of analysis and detection mechanism by analyzing a greater variety of diversified data such as Domain name system transactional data (using apache spark), identification of social media data (click streams, like, shares, comments and posts) either by using some tools like apache flume that directly connects to a data dumping mechanism like transferring the data from a live stream to HDFS using API and then.
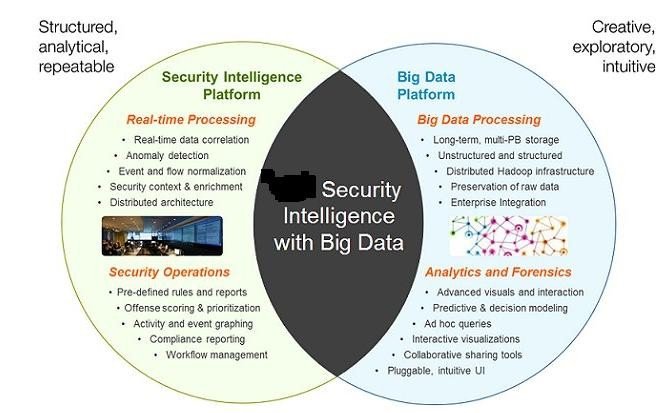
Q Radar works with structured as well as unstructured data and sometimes it is compatible with semi structured data with these capabilities, this tool is sufficient enough to identify the risks and flaws and in always providing a scope for continuous learning and closed loops. These result in an integrated environment where a person can share, monitor, explore different possibilities amongst various reports on security and can share along with any product (either apache Hadoop or any other big data platform). Some of the major capabilities of using Q radar are: that it always consider real time correlations with anomalous data detection (behavioral analysis where tools can detect overall compliances and functionality of servers that are storing critical data like healthcare or insurance data). This results in high speed query to intelligence data and improving overall intelligence system structure. Q Radar also provides a well explained and well defined front end tool for better data visualization and exploring other functionalities of big data analytics. It has access to various domains of data like emails, critical documents, full packet capturing of data, and business process data (BPD) that is often used with various business intelligence systems. It helps in depth analysis of forensics investigation, thus helping to reduce the risk of data lost and infringement.
Conclusion
This article speaks about how big data is helpful in cyber-crime detection and more often it says about how the things can be managed and become easy when the analysis part becomes strong while analyzing complex data sets and variety of data. It usually becomes a compulsion to improve the techniques that can be embedded in order to avoid/ prevent cyber-attacks and cybercrimes as well.





Very informative blog. I was looking for some good information about cyber security and finally I got something useful information. Thanks
Thanks for sharing this information on cyber security