In the current generation, cloud computing has become a buzz word. Gone are the days when data were used to be saved over disks. Since then the concept of data sharing has evolved exponentially as forget floppy disks, now even CD’s has become the thing of past. Today, devices for sharing data are becoming smaller with higher capacities. Now, we don’t need to save all our documents instead we can access it from cloud storage.
So, what really is cloud computing?
Here, the cloud is used as a metaphor for the internet. In simple terms, cloud computing can be referred for storing data over the internet which can be retrieved through web-based tools or applications. It eliminates the need for storing data over personal devices such as hard drives, USB flash drives or any local storage device.
For the better insights of Cloud computing, you can refer my previous article ‘Cloud Computing: Things you must know and Understand’.
This article mainly focuses on the architecture of cloud computing, its benefits over conventional storage techniques and security. So let’s start with the architecture first.
The Architecture of Cloud Computing
To understand the working and architecture of a cloud, we need to take a deep look into its components and establish significance for each one of them. The cloud components are loosely coupled. In other words, they are independent of each other. Let us see what cloud is made of.
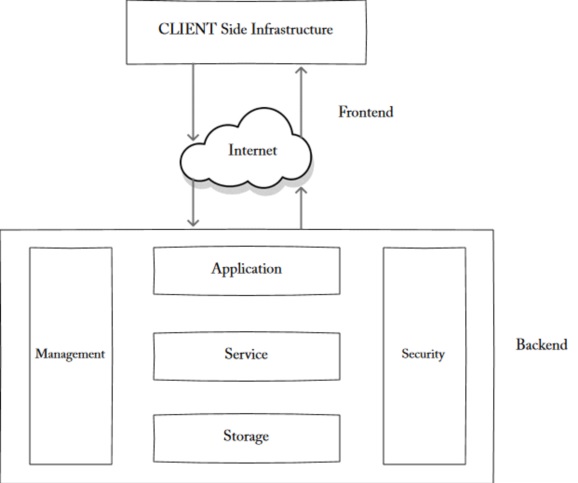
Front End
The front end of a cloud belongs to the client side. This part of cloud computing is managed by the client. This comprises interfaces and applications that are required to access the cloud. For example, we generally use a web browser like Google Chrome or Mozilla Firefox to access the services that are available in the cloud through the internet.
Front-end components include the user interface, along with the client’s computer system that is utilized for harnessing the cloud system. There is a provision where all cloud computing services have different interfaces for users to learn and manage—for instance, the Google Docs user interface is distinctive than that of Salesforce cloud interface.
Back End
The back end of a cloud belongs to the vendor who is managing the entire cloud. It comprises of all the necessary components that are needed to run a cloud. It has data storage, virtual machine, security mechanism, services, deployment modes, and servers. CSPs are responsible for the functioning of all these components.
Internet
The most mandatory component required to pull off this setup is, of course, the bandwidth. It connects both the client and the vendor and enables a smoother flow of data. To sum it up, cloud computing services can be found everywhere these days. If a user is utilizing services like Google Drive or Office 365 at home or work, then he is a dedicated cloud computing user.
Let’s discuss some important types of architectures which can vary depending on the business requirements.
Single Server
Single server cloud templates embody the use of one server, physical or virtual, that includes a web server, an application, and a database. Single server architectures are not widely used, as they have potential security risks which can compromise the whole system. These architectures are usually deployed for development purposes, enabling developers to strengthen functionality without having to deal with connectivity and communication issues between different servers.
Single Site
Single-site platforms utilize the single server architecture and divide the layers in different systems thus modeling a three-tier architecture. As the system is administered in the same location, single-site architecture is maintained as up and running.
Redundant three-tier architectures
Redundant three-tier architectures have the capability of appending another set of the same components to look after redundancy. These pairs of components increase the complexity of the system but are required to tackle failover and manage recovery protection. Constructing redundant infrastructures requires a well-executed plan for the components within each layer for horizontal scaling, along with a plan for how the traffic will circulate from one layer to another meant for vertical scaling.
Auto-scaling architecture
The main takeaway of cloud computing is the ability to utilize a particular service or resource when it is needed. This autoscaling feature enables the cloud to scale horizontally which is to shrink or grow the number of running server instances in a largely coupled system with changes in demand of application over time.
Different sorts of architectures are supplied to the clients. It is the responsibility of the client to make sure that the model he prefers for his business must suit his business needs and requirements in the long run. At times, it is necessary to gain information regarding cloud from the vendor to ensure smoother execution of applications and work-flow balance.
What Benefits does Cloud Computing provide compared to Conventional Storage Techniques?
Traditional storage techniques include data centers that comprise of hardware infrastructure like a desktop computer which is connected to a network with the help of a remote server. This server is responsible for granting employees access to the business’ stored agenda and applications.
Those who rely on traditional strategies to deal with their business requirements have access to it all the time through a remote server. The components required to run this server includes both hardware and software which are obtained by the company. A team of IT professional looks into the system and administers it. They have the responsibility of updating and making changes to this system when needed.
Whenever a debate between these two topics goes head to head, these sub-points can be useful to support your discussion.
Assurance of data not getting lost!
The data and applications which are hosted in the cloud are uniformly dispersed across all the servers, which are connected all the times to work as a single unit. Even if a server fails at the wrong time, there are other servers which are online to take care of that. This means that no data is lost and the uptime is constant throughout the whole process. Compared to traditional techniques, the cloud has the capability of providing more storage space and server resources which encourages more computing power and speed. This enables better utilization of available resources for the software and applications to perform at their prime.
Scalability
The scalability factor is enough for some organizations to prefer cloud to its counterparts. Traditional technologies have a limited scope of expansion due to the limited availability of servers. You have to pay for more servers if you want to expand your base. Cloud eliminated this problem by providing a platform which gives you unlimited space and access to resources anytime. They can scale it up or down depending on the company’s demands and requirements. Plus it gives a sense of control to the company over their data and applications. This helps in maintaining the flexibility of the company.
Traditional approach doesn’t encourage the expansion to handle more workload without buying new servers. This doesn’t solve the problem and may increase the downtime which can cause heavy losses to the company.
Expenditure
Traditional techniques have the ability to expand at the cost of adding more servers which invite more expenditure. Whereas, the cloud comes with an affordable price tag at the cost of providing all the features and services that an organization needs to keep growing in the long run.
At times, buying a traditional infrastructure can become tedious and out of control as there are many components involved. This can incur huge budget shift for the organization and disturb their operating costs. Cloud vendors present a host of different packages which can be suitable for any type of business expansion and overall development.
Automation
Cloud computing has automated businesses all across the globe thanks to its premium hosting services. The vendor takes care of the cloud from a single system and manages them all at once. Managing a traditional system is a lot more time-consuming and tiresome as the company has to hire more people to manage each component separately. A cloud service results in less headache for a company who has to manage a lot of elements and keep them up and running all the time.
Integrity
Data security and integrity is maintained all the time in the cloud. Unlike its contenders, the cloud has a different security mechanism which ensures data integrity and confidentiality. Nowadays terabytes of data are being generated which enables the analytical companies to store this data in order to derive meaningful business insights in the future. Data is gold in today’s era and enterprises need to take good care of it.
Security and Safety Threats

Most companies at a senior level of any implementation consider the safety and security concerns of that system. Whether, it is a software or any hardware, along with several perks they bring a whole new level of alarming threats that can invite a lot of obstacles to a company’s growth. While the cloud has helped many companies scale their business, it has several security vulnerabilities.
Data Breach
The year 2018 will be remembered as the year of the maximum data breaches. Many big organizations like Facebook was booked for allegations which involved breaching of millions of customers’ data. This data breach shocked the entire tech industry and people started questioning the safety of data in the hands of these big corporations. One more similar incident was reported by Equifax where it released a statement saying that in 2017, around 143 million customer’s data was compromised. This is the problem you face when you have to maintain a humongous database comprising of more than 100 million people.
Trojan Horse
The main pillar for any company is its human resources, that is, its employees. Most of them work in a protocol that helps the company with its normal functioning. But, at times they are people who take the wrong route and might leak their company’s vital and confidential data through various means like social media or external pressure. This cannot be avoided as the cloud won’t be able to detect and tackle it. This causes the company to take some extreme steps and look after its data with extra precaution.
Vulnerable APIs
Cloud Service Providers or CSPs manage a collection of application programming interfaces (APIs) that customers use to operate and communicate with the cloud services. Companies use APIs to conduct, orchestrate, and keep a track of their assets and potential users. These APIs can be accessed through the internet by their CSPs. They are equally vulnerable as an operating system and its libraries which can be accessed from anywhere online.
Support Issues
Companies can face the issue of compatibility when launching their applications in the cloud.
There could be certain products that companies need to launch within a span of time. Implementing the same in the cloud could be feasible but it would require the company some time. For launching it in the cloud, it should be able to support the cloud in means of its APIs, orchestrators, functions and its level of competency.
Insufficient data backup
Data in the cloud is stored in many forms and at different locations. This could be located anywhere and can be accessed from anywhere. At times, when a particular batch of data is being deleted, only 60-75% of it will be erased. Rest will be kept in the cloud in various chunks which won’t be easily accessible for further deletion. Similarly, if the original copy of this data needs to be accessed from the server, it won’t be plausible as that part of data is now corrupted.
Lack of trust
This occurs when the cloud vendor and the company have signed an MOU but are in bitter terms about having a mutual trust with each other. This will cause CSP to increase the prices of the cloud services while limiting any premium services for the company. This can lead to under-utilization of resources by the company which will result in complete chaos.
So, this was it! Hope you got a better insight into the architecture of cloud computing, its benefits and security threats.



