
Introduction on CISSP Tutorial
Welcome to CISSP; the world’s most appreciated and recognized Certificate in the Field of information systems security. In this series of articles, we are going to discuss in great details all what you need to become a CISSP. So, put your seat belt, and be ready to takeoff.
What is CISSP?
CISSP (short for Certified Information Systems Security Professional) is a vendor-neutral certificate that is controlled and backed by (ISC)2. Being a CISSP proves deep understanding of the necessary security concepts and skills required to implement, manage, and maintain a secure information system environment.
CISSP covers the following security domains:
- Security and Risk Management.
- Asset Security.
- Security Engineering.
- Communications and Network Security.
- Identity and Access Management.
- c and Testing.
- Security Operations.
- Software Development Security.
Why to Care about CISSP?
The following are good reasons to become a CISSP:
- To widen your security knowledge.
- To increase your competitiveness in the labor market.
Furthermore, even if your are not planning to certify, or don’t yet meet the minimum years of experience required to be a CISSP (5 years experience in Information Security field), you are still encouraged to study CISSP. CISSP will broaden your security knowledge as we said above. CISSP is usually said to be an inch deep and a mile wide. This means you will gain huge security knowledge on different security aspects, which belong to the eight security domains mentioned above. The best expression that accurately describes this fact is the Arabian expression “a rose from each garden”.
How to Become a CISSP?
To obtain the CISSP certification, you need to:
- Pass the six-hours exam, that consists of 250 multiple choice questions, with a minimum score of 700 points out of 1000.
- Study this series first.
The CIA Triad
What does Security try to achieve? Or to be more accurate: what is security trying to protect? Or in its simplest form: what all this for?
Generally, Information Security aims to ensure three main aspects:
- Confidentiality.
- Integrity.
- Availability.
This is what is usually referred to as the CIA Triad (C for Confidentiality, I for Integrity, and A for Availability).
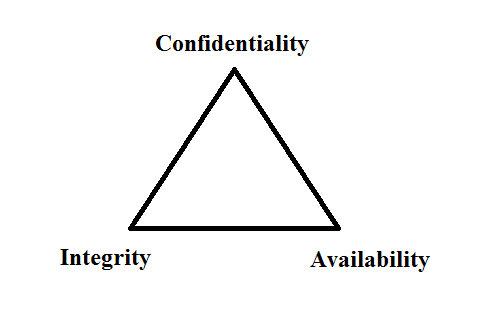
Now, let’s understand the meaning of each principle.
Confidentiality
Confidentiality aims to maintain the secrecy of information. In other words, only authorized personnel should have access to the organization’s sensitive information. A company may be subject to huge fines, bad reputation, hence financial losses, and may be a complete kick-out of business at the end as a result of being unable to protect the confidentiality of their data.
Data Confidentiality must be maintained both:
- At rest: where data is stored.
- In transit: while data is being transferred in the network from host to another.
Many types of attacks target to break confidentiality to obtain unauthorized access to classified information. Such types include – but are not limited to – sniffing network traffic, breaking the used encryption, social engineering, and shoulder surfing.
Protective countermeasures are employed by organizations to prevent such unauthorized disclosure of sensitive information. Commonly-used countermeasures include authentication, access control, data encryption, using secure protocols for communication, and training staff to enhance their security awareness.
Integrity
While Confidentiality cares about unauthorized read of data, Integrity cares about unauthorized write (alteration) of data. So, integrity aims to assure data accuracy and reliability.
Integrity should:
- Prevent unauthorized personnel from altering data.
- Prevent authorized people from performing unauthorized modifications on data either accidentally or maliciously.
To protect integrity of data, protective countermeasures may not be sufficient alone; so detective countermeasures are also needed. Protective controls that help ensure integrity include authentication, access control, data encryption, using hashes. Detective measures include using Intrusion Detection systems, logs, and audit trails.
Availability
Availability aims to guarantee that data and system resources are available to authorized people on need. The most popular type of attacks that targets data and systems’ availability is the Denial of Service DOS attack.
A considerable amount of threats that can badly affects systems’ availability comes is due to environmental issues. Unstable electricity with surges and spikes may damage a server’s power supply, and even worse its motherboard. A complete electricity blackout with no redundant and independent power source, and no UPS with efficient batteries will mean simply that systems will be down and hence not available for use. Insufficient Air Conditioning and temperature control in the data center room could have similar effects.
Failure to protect systems and data availability has direct negative consequences like: customer dissatisfaction, and bad reputation.
Protective countermeasure include: using redundant and independent power sources, uninterruptible power supply UPS, electrical generators, data and system backups, having Disaster Recovery DR Site, and complete efficient Business Continuity Plan BCP.
Who is Concerned with What?
Of the three main principles of the CIA triad, which one should I give more care?
Actually, that is a question that has no one determined correct answer; each organization has its own priorities, which in turn dictates caring about one or more of the three CIA security aspects.
For example, a military authority will give ultimate importance to protecting information’s secrecy, so it will be concerned with Confidentiality. On the other hand, a bank will pay more attention to protecting the Integrity of their data (data here means money), and will care with less degree about Availability.
Summary
- CISSP is the world’s most recognized and appreciated security certificate.
- The CIA Triad describes the three main security aspects: Confidentiality, Integrity, and Availability.
- Confidentiality is concerned with protecting secrecy of data.
- Integrity aims to ensure data accuracy and reliability.
- Availability aims to guarantee that data and system resources are available on a timely manner when they are needed.


