Security is no longer considered to be some sort of luxury. Today, being adequately secure is vital for companies to survive and stay in the track of the wild market competition. Accordingly, organizations are now giving increased importance to the security-related issues. Each organization should have its own security program that reflects and ensures to which extent the organization is concerned with reaching and maintaining a good security posture. This article is our start with the Security Governance subject. So, let’s get started.
Security Governance
What is Security Governance? This is the first logical question to ask.
Security Governance can be defined as the set of practices that an organization undertakes including developing strategies, achieving objectives and ensuring that they use all their resources to mitigate security risks and maintain a good security policy.
In any organization, security is not the responsibility of one particular person or team. Actually, security is the responsibility of everyone; starting from the newest junior, and up to the top management.
To achieve and maintain a good security policy, an organization needs to develop an effective security program. The top management represented by the board of directors should be involved in this process as follows:
- The top management should be the main sponsor of the organization’s security program.
- They should support and encourage staff to contribute to the success of the security program.
- They should allocate the necessary budgets required to purchase technologies, licenses, and train staff.
The involvement of the top management is essential to illustrate and ensure the commitment of the entire organization in risk mitigation and security enhancement efforts.
Due Care and Due Diligence
Two important terms that you will encounter frequently are due care and due diligence. The difference between the two terms is sometimes tricky. That is why many people confuse them. The following are the definitions both terms:
Due Care: Due care refers to the organization ensuring it has done everything in their power to mitigate any security threats against their system and their company. It suggests that the company, takes all the necessary means to ensure that it is protected against treats.
Due Diligence: Due diligence is when the company continues to monitor and update its systems with appropriate and updated systems so that their security is not compromised.
To illustrate the difference, the best way is to take an example:
In your company: selecting and purchasing good antivirus software, and deploying it on all machines is considered a due care activity. The continuous monitoring of the antivirus logs, antivirus definition updates, and confirming that client software is working properly on the hosts is considered a due diligence.
Strategic, Tactical, and Operational Plans
Security Governance requires the top management sponsorship, commitment, and continuous direct supervision of the security program implementation efforts. So, the top management should be involved in all phases of the security program cycle.
– Sorry, did you just say something like “cycle”?!
Yes, what you heard was ultimately correct; security is not a one shot project. Rather, it is a continuous cycle.nted controls.
Definition
The security life cycle or the security wheel is a continuous process that consists of several consequent phases (stages). The word cycle indicates the continuous and endless nature of such process.
The ISO 27001 defines the cycle of the information security management system ISMS as PCDA: Plan-Do-Check-Act.
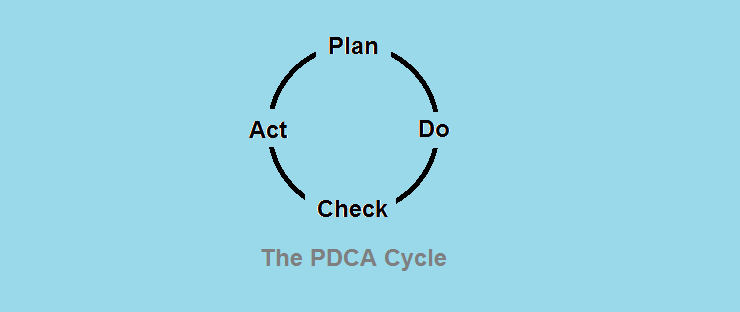
Other sources use another equivalent approach, the Secure-Monitor-Test-Improve model:
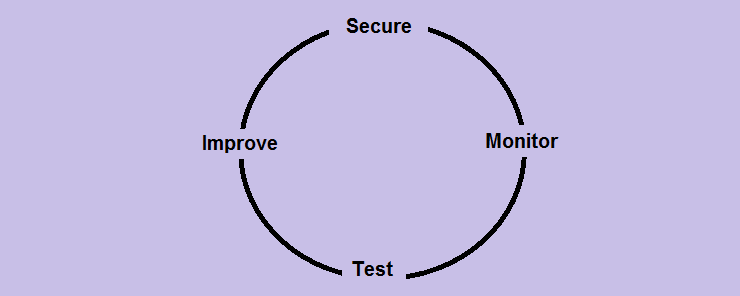
The approach works as follows: the company implements security countermeasures to defend itself and secure its data and premises. Next, the newly-implemented controls are passively monitored to evaluate their effectiveness. Next, the testing stage; in which the environment is tested either by internal security staff, or by outsourced third party. Upon the completion of the testing process, a detailed report of the findings from both the monitoring and testing stages should be prepared and delivered with recommended actions to the concerned parties in the company. Recommendations in the report are then used to improve the currently implemented controls.
As with any project, good and careful planning is essential for the company’s security program success. Such planning should be made on three levels: strategic, tactical, and operational.
Strategic Plan
The highest level of the three plans. It describes the organization’s vision and goals for the long term (typically for 5 years) concerning security. The strategic plan should be reviewed and updated on an annual basis.
Tactical Plan
Following the high-level strategic plan, the tactical plan includes details and other information that suggests how the strategic plan can be executed. . In other words, while the strategic plan is concerned with the general vision and goals, the tactical plan takes you one step down to the details of how to achieve such goals. The tactical plan is prepared for the mid-range (one to two years). Tactical plans usually contain projects, budgets, contracts, and resource allocations.
Operational Plan
The lowest level plan that goes down deeply into the small details. The operational plan is meant to address how to implement (in step-by-step procedures) the previously-set tactical plans. Operational plans are made for the short term (weeks and months).
Top Management Role
Without the continuous commitment and support from the top management, all the above plans and efforts will be useless. So, the top management support is crucial for the security program to succeed.
Summary
- Due care is to act responsibly.
- Due diligence is to do all the necessary tasks required to maintain the due care.
- Security is a continuous process, not a one-shot project.
- There are three levels of security plans: strategic, tactical, and operational.
In the next article, we will talk about Risk Management. It’s bound to be good, so wait for us.









