The internet is currently flooded with teraflops of data which is utilized by tons of netizens all over the globe. This data includes all sorts of information which help us with our curiosity towards a certain topic and keep us informed about it. In this article, you will learn about DDoS attack.
It is a place where any kind of data is freely available and that is without a doubt extremely beneficial. But, as every story has two sides to it, there are many illegal users and hackers present on the internet that deploy malicious software and cranky bots that attack a particular host by flooding its network with tons of network packets. These attacks have become the emerging cybersecurity threats of 2019.
This leads to disruption of that network which leads to denial of any kind of service in-and-out from that network. All the systems that are connected in this network get affected and can’t send or receive any data within this network. This is the Denial-of-Service (DoS) attack which is carried out by the infiltrator to attack and seize the resources of the victim host.
An Overview of a DDoS Attack
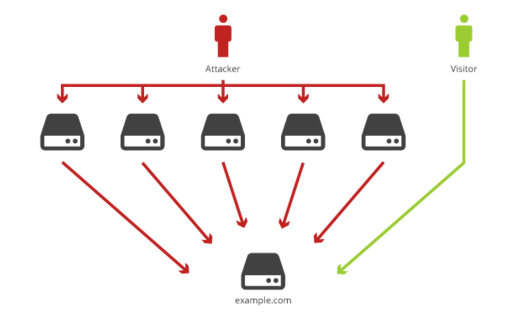
Distributed Denial of Service attack or DDoS attack is another type of DoS attack which is carried out by multiple sources to avoid tracing it and later disabling it. It can be implemented by setting multiple systems with buggy software or malicious application. It will then be instructed to send multiple packets of redundant data to a single source.
These applications that are loaded at various sources then flood the victim network with gallons of useless packets of data in order to create a ruckus in the network and in the end, disabling it in order to affect its business.
The DDoS attack is not easily traceable as it is performed from multiple sources which make it difficult to stop as well. Hackers and cold-blooded netizens who want to exploit a particular server carry out this operation for their benefit.
At times, a DDoS attack can be performed to check the security and firewall capabilities of a network in order to check if it is safe for other users to access. There are many updates done daily in a website of a bank or an enterprise which might pose a risk to its users. They share their sensitive data like credit card details, contact number which can be easily compromised if the network security is not strong and reliable enough.
The span of a DDoS attack totally depends on the layer which got affected. In case of a network layer, it will last for up to 50 hours at maximum capacity. The application layer is the worst affected as it remains for 75-80 odd days.
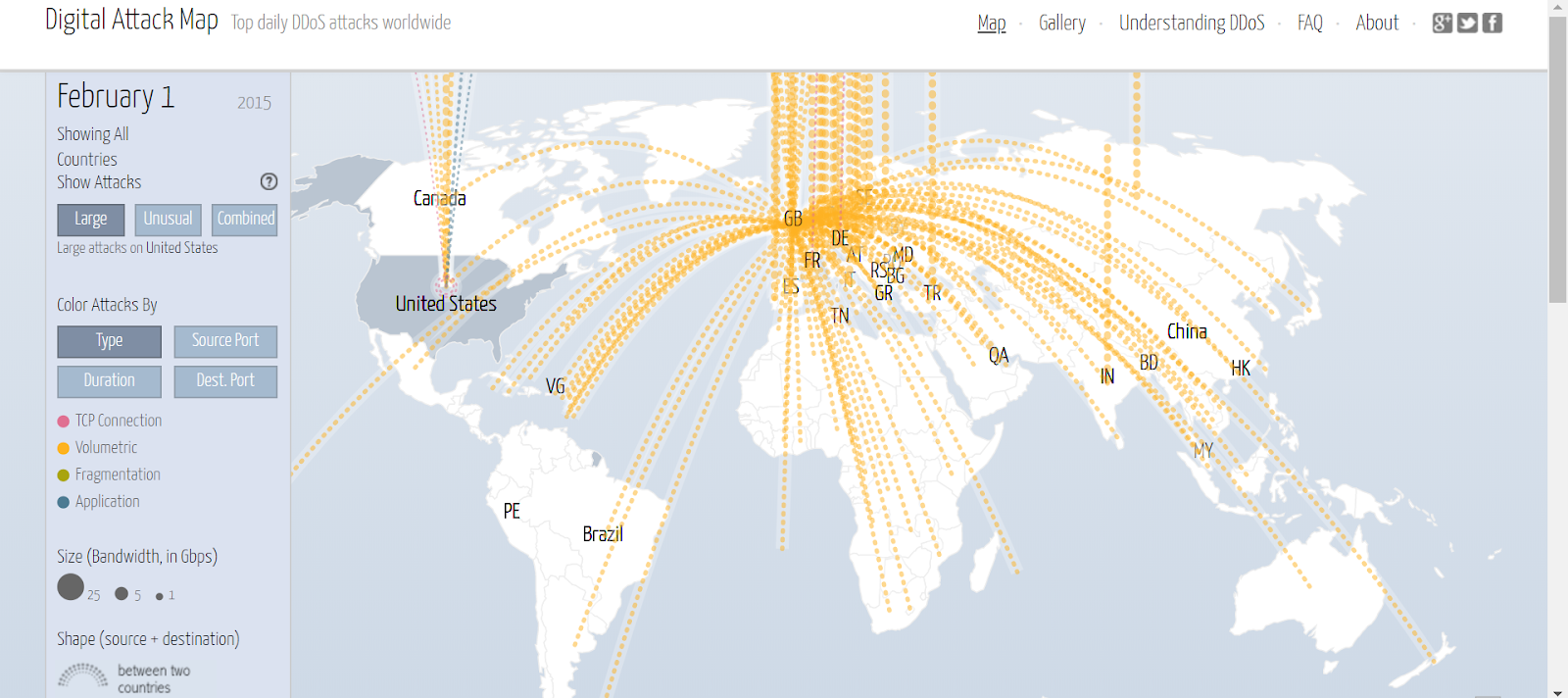
The above map displays the various DDoS attack that are being carried out on a real-time basis. Every day, millions of data files are transmitted to different sources across the globe and all the countries present on the globe are a victim of this attack. Infiltrators have learned and mastered the technique to exploit a network even if it is secured by a strong firewall.
These attacks can be divided into 3 types.
- Volume-based
- Protocol-based
- Application-based
Top 3 Powerful Kinds of DDoS Attack That Shook the World
-
Github
Feb 28th, 2018 witnessed the biggest DDoS attack in the history of invasions. Overall, an intrusion of the traffic of 1.35 Tbps was recorded in this attack. No website has ever encountered anything like this before! Github is one of the biggest web-based file hosting service used for sharing codes in all languages. Never in its wildest dreams, anyone at Github would have thought of such a catastrophic attack, crippling its servers and disrupting its services. It not only helped GitHub understand how important it is to be ready for such attacks but also they upgraded their security to a scalable extent.
-
CloudFlare

Content delivery website CloudFlare was attacked by approximately 400 Gbps of data. This attack happened to a lot of users in Europe and was done by attacking the Network Time Protocol(NTP). The attacker used a technique in which unknown source addresses were utilized to send massive amounts of NTP servers. This can also be termed as reflection, as the attacker was able to mirror and multiple the traffic of packets in the network.
-
Banks
Banks from time to time have been targeted by various infiltrators for their sensitive data of customers. But the one that stands out is the one that happened in 2012, which targeted a total of six banks, where a string of DDoS attack was carried out from different sources. This included some of the famous banks like JP Morgan, CitiGroup, and PNC Bank. The infiltration was caused by hundreds of malicious servers, where traffic of 60 Gbps was recorded. This attack was carried out by a multitude of sources from around the world by using different techniques of attacks that made these banks that were employed to tackle these attacks both hapless and helpless.
Tons of such DDoS attacks were carried out in different servers by different sources which made them difficult to trace.
So, How Can We Get Rid of Such Attacks?

Basically, the frequency of such attacks and other cyber attacks has increased at a pace which can’t be controlled at any cost. More importantly, it is difficult to detect such attacks in advance and prevent them, however, there are some key steps which any individuals can take to recover from these attacks. Better to learn from earlier mistakes and not repeating them in the future.
Meanwhile, you can also read this useful piece of information on “The Best Ways to Protect Yourself from Cybercrimes” for getting the detailed insights into Cybercrimes, Cyberattacks and the Ways to Prevent Yourself from these Attacks.
Let’s see some of the techniques which can be deployed to strengthen our network base.
-
Developing a strong network infrastructure
Building an infrastructure that can easily back levels of network protocols is necessary for a good network security system. This comprises of firewalls, VPNs, content filtering, and spam filtering layers which are mandatory for any network security. These components ensure that any such attacks don’t have much of a chance of attacking your systems and you can be reliant on this option.
-
Bringing the cloud in
Migrating the DDoS system to cloud can prove beneficial in the long run due to scalability and more bandwidth. With more infrastructure available at hand which can be utilized anytime for any amount of data that be redirected to the server, a properly-planned cloud infrastructure can be incremental for any company.
-
Warning signs!
There are some warning signs which can be detected well before the attack. Signs like less network speed compared to the original speed, unusual activity on the website, decrease in the performance and speed of the website and unusual traffic which can be detected quite easily well in advance before the attack. Continuous monitoring of network analytics is a fundamental way of detecting such warning signs and stop them before they create any ruckus.
End Notes

The amount of data is increasing at an exponential rate due to the inclusion of data collection techniques. These data should first go through a good filtration system that should be planted at every network switch to increase security. Precautions need to be taken in order to avoid any catastrophic attack that has the capability of wiping the entire database which has data of billions of users. It will be crucial to see how companies tackle this mounting issue with the help of resources available in hand and maintain the network integrity at its prime.
If you too want to protect your internet from any unknown intervention, you can try out the “CompTIA Cybersecurity Analyst CySA+ (CSA+). The Total Course“. The course comes with 7 hours of video covering 17 sections and is taught by former military intelligence personnel.
Or if you want to learn about security to protect your personal devices, you can try out the “Cyber Security For Normal People: Protect Yourself Online” online course. The course comes with 1.5 hours of video that covers 7 sections with topics such as multi-factor authentication, Google two-factor authentication, Encryption and many more.



