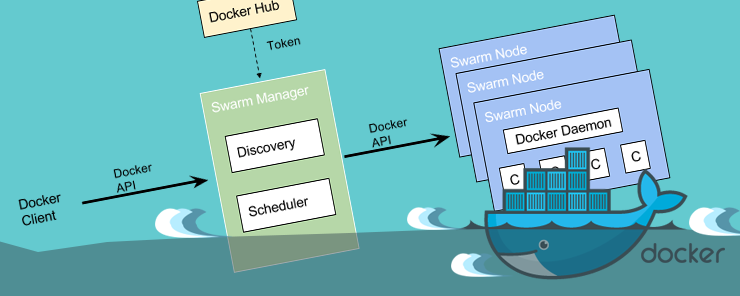
Learn How To Use The Docker Api To Manage Containers And Images
Within the Docker ecosystem there are three APIs available. These are the registry API, the Docker Hub API and the Remote API. The...
Learn Object Oriented Programming in Python – Inheritance
The Concept
In the last article (Object Oriented Programming in Python - Classes and Objects); we talked about the main benefits for using OOP approach...
How To Configure Remote Access for MongoDB on Ubuntu
MongoDB is a free, open-source and document oriented dtabase commonly used in modern web applications. By default, MongoDB listens on localhost and is configured...
Learn How To Use Functional Data Structures In Scala
In a functional programming style modification of variables is not allowed. The big question that comes to a programmer is what type of data...
Developing Secure Applications Part 4 Secure MicroServices
In part 2 and part 3 of Developing Secure Applications series we have looked at OpenID connect and OAuth2 using the excellent WSO2 identity...
Learn Iteration using Loops in Python
In the previous article (Part 5 – Decision making using IF Conditions), I told you that life never goes one way. Actually, life in...
Learn How to Monitor AWS CloudWatch with Grafana
Cloud computing might be one of the best ways to host the applications. However, it takes dedicated effort to manage cloud applications. Also, it...
Learn how to use Python as a Web Developing Language
So far, we have seen how Python could be used as a scripting language, Object-Oriented Programming language, and GUI Applications factory. Now, we will...
Learn How to Scale a Kubernetes Cluster
Application scaling is one approach that can be used to dynamically allocate resources. However, it has its limits and sometimes all node resources are...
Learn How to Improve Security in Software Development
The target of cyber attackers have shifted from websites to software in the past few years. It’s often said that performing security testing simultaneously...